HashiCorp Vault Integration with Ansible Etower using approle
HashiCorp Vault is a secrets management tool specifically designed to control access to sensitive credentials in a low-trust environment. It can be used to store sensitive values and at the same time dynamically generate access for specific services/applications on lease.
Integrating the vault with Ansible Etower provides robust and secure automation.
Following is the step-by-step guide for the integration.
- Enable key-value secret engine in Hashi Vault (also known as "kv" engine). Let's call the engine, the "kv" engine.
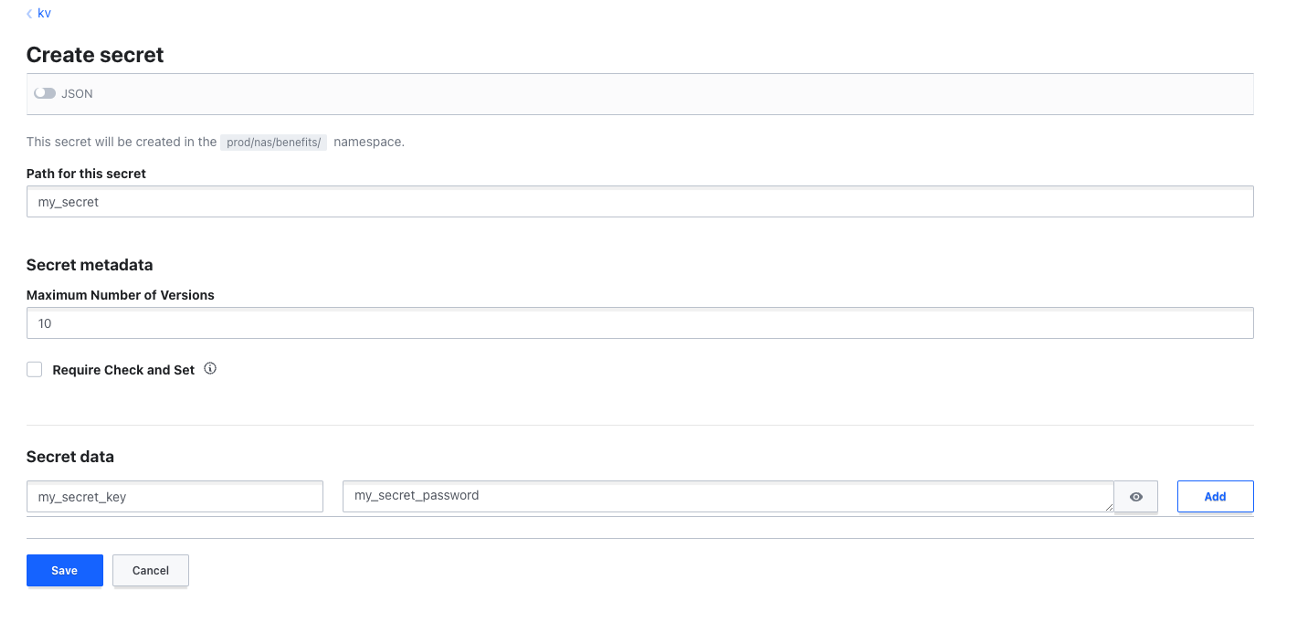
- Create a secret inside "kv". A secret can be a collection of key-value pairs or a JSON for nested structure.
Lets assume that secrets are stored as JSON in the format
{"my_app":{"service_account_name": "some_service","service_account_password": "some_password"}}
- Create a secret policy defining what can be done with the above-defined secret.
- Create an "approle". AppRole is an authentication mechanism within Vault to allow machines or apps to acquire a token to interact with Vault
> vault write auth/approle/role/test-role
- Attach policy created above to the approle
> vault write auth/approle/role/test-role policies="my_secret_policy"
- To access this KV pair without using your personal token requires setting up a "role_id" and a "secret_id". You can think of this combination as a username and password pair.
> vault read auth/approle/role/test-role/role-idKey Value--- -----role_id 3c48fdd3-60e0-4ab1-afd1-9e7406ce301b> vault write -force auth/approle/role/test-role/secret-idKey Value--- -----secret_id 1d399f8b-19af-443d-8568-1d0793dd90f8secret_id_accessor 46c16a28-07c4-43a1-9c5a-d7df575ac628
- To create "role_id", you need to use commands as this support is yet not present on the graphical interface. You can set same on your local machine or use console provided on vault UI.
At this point, Hashi Vault is configured to be used with Ansible and Etower.
Lets see how to use this configuration inside ansible playbooks.
Steps for Ansible Etower.
- Choose or create a credential type to store three parameters to be used to interact with Hashi Vault in Etower. This way you do not need to expose these secret abusable data inside your open playbooks.
- Vault URL (There can be multiple vaults in your organization, let the variable name be "vault_server")
- Vault "role_id" (Let the variable name be "vault_server")
- Vault "secret_id" for the "vault_role_id" (Let the variable name be "vault_secret_id")
- Use the above-created credential in your Ansible template, as per the example code below.
- name: Hashi Corp Integration
gather_facts: true
hosts: localhost
vars:
VAULT_ADDR: '{{ lookup("env", "vault_server") }}'
VAULT_ROLE_ID: '{{ lookup("env", "vault_role_id") }}'
VAULT_SECRET_ID: '{{ lookup("env", "vault_secret_id") }}'
VAULT_NS: "some/name/space/"
VAULT_SECRET_PATH: kv/data/my_secret
app_name: my_app
tasks:
- name: setting facts for vault
set_fact:
VAULT_ADDR: '{{ VAULT_ADDR }}'
VAULT_NS: '{{ VAULT_NS }}'
- name: "Connect hashi vault at {{ VAULT_ADDR }} with namespace {{ VAULT_NS }}"
set_fact:
vault_details: "{{ lookup('hashi_vault','secret={{ VAULT_SECRET_PATH }} auth_method=approle role_id={{ VAULT_ROLE_ID }} secret_id={{ VAULT_SECRET_ID }} namespace={{ VAULT_NS }} url={{ VAULT_ADDR }} validate_certs=False') }}"
no_log: true
- name: "Fetch app_role and password from Hashi Vault at {{ VAULT_ADDR }} and namespace {{ VAULT_NS }}"
set_fact:
service_account_name: "{{ vault_details.data[app_name].service_account_name }}"
service_account_password: "{{ vault_details.data[app_name].service_account_password }}"
no_log: true
- name: print the password
debug:
msg: '{{ service_account_password }} -- {{service_account_name}} '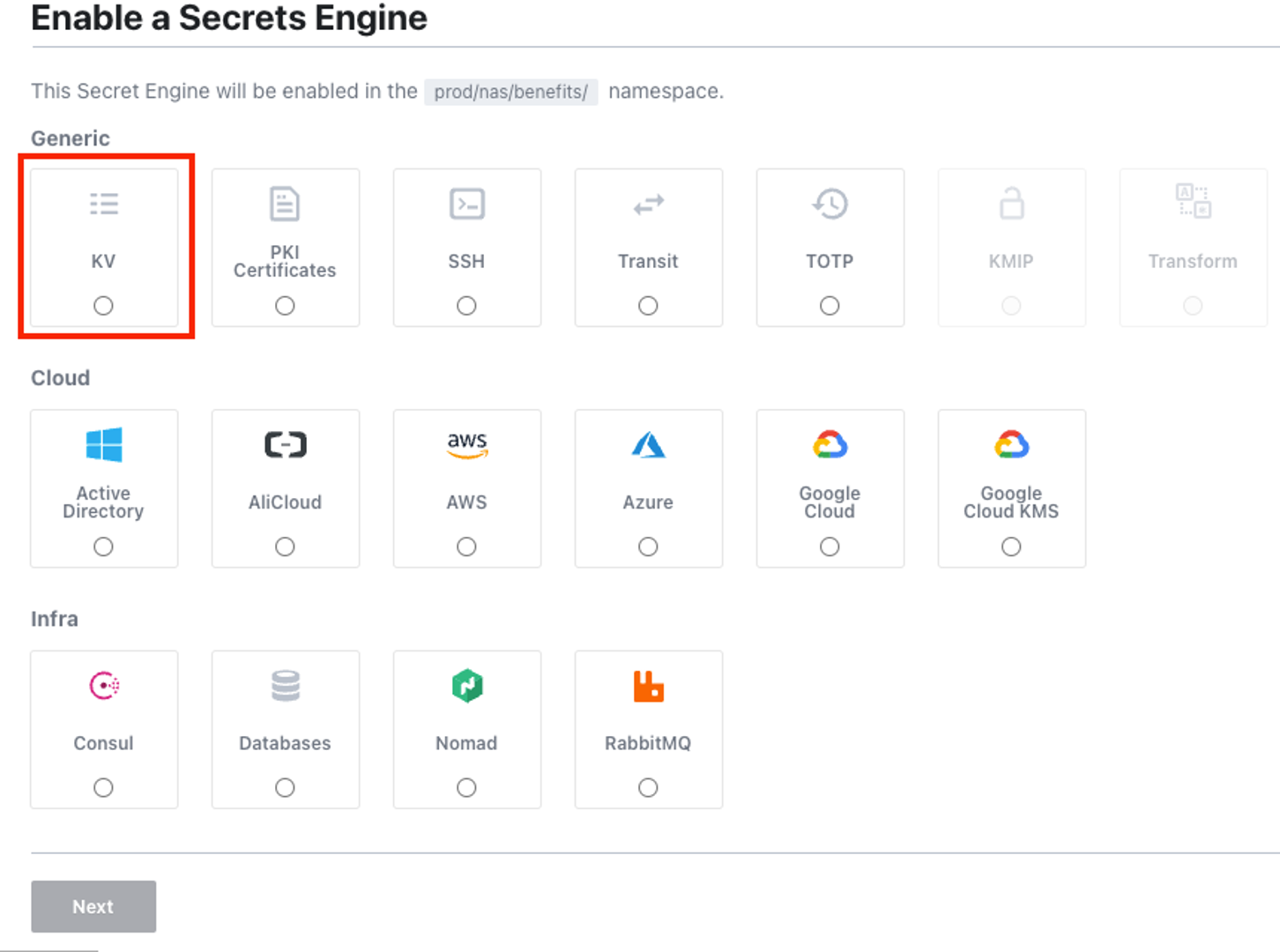



Comments
Post a Comment